There’s a vast difference between hackers and attackers, which is used in the above crafting as hackers are just experimental people. In distinction, the latter will come underneath the group of criminals in computer systems to get access to their data.
In no way. We unlock your phone 'About-The-Air' using 3G/4G or WiFi or by sending you an Unlock Code - our method is completely remote. Your phone is secure during the full course of action and there'll be no interruptions to your service.
On top of that, when exporting, you are able to decide to composition the data into a selected template suitable for import into the largest targeting marketing tools. How can I access the Gallery on someone else's smartphone? Can I delete photos? Accessing Gallery lets you view photos and videos, view help specifics of them, conserve them to your AppMessenger account, or download them to your device. You can't delete photos.
Alerts for suspicious activity: The warning signs of the VoIP hack can incorporate an influx of calls, far more Worldwide calls, or logins from other devices. Try to look for a VoIP provider that alerts you when this stuff occur in order to remove the danger.
Nextiva is shaping the way forward for growth for all organizations. Start out Understanding how your company will take almost everything to the subsequent level.
If your cell phone Monthly bill arrives back greater than anticipated, this may be a sign that your phone has malware. This is for the reason that spyware or malware consistently runs on your phone, ingesting up data usage.
The 1st and best spy application You need to use to hack into someone’s cell phone is mSpy. This application is compatible with Android and iOS mobile devices and may even be mounted remotely. It offers a good amount of attributes, many which don’t involve you to root or jailbreak your device.
But Certainly, you will find other methods to get wireless connectivity. Some have to have this kind of Excessive tolerance that the café idea will start out wanting very good. Read on, if you can't wait.
The best way to hack Android phones remotely using cloak hack phone remotely with cmd and dagger assault – this process is for Android phones only;
Apple iPhones is usually compromised and their delicate data stolen through hacking software that doesn't require the phone's owner to click on a link, Based on a report by Amnesty Intercontinental published on Sunday.
Altough you are able to’t change Intelligent Lock or password configurations without moving into your recent password, it remains to be exceptionally helpful to backup important files. Once you receive back every thing, you required you can do a factory reset.
Step 1: Go to the Formal Cocospy website to register for the service. Whilst at it, select a approach that suits your hacking demands.
Regardless of its ominous identify, bloatware, or pre-downloaded apps on your phone, may be ordinary. But in case you notice your phone has new apps you didn’t buy, this might be an indication that a hacker has access to your phone.
"As an added precaution, we advise turning on two-aspect authentication, called Login Approvals, in your Facebook protection settings. Carrying out this will disable recovery by means of SMS on your account so even if someone has your phone number, they'll still require your password to access your account."
 Barret Oliver Then & Now!
Barret Oliver Then & Now!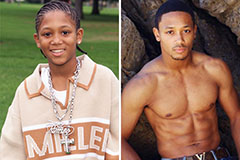 Romeo Miller Then & Now!
Romeo Miller Then & Now! Ross Bagley Then & Now!
Ross Bagley Then & Now!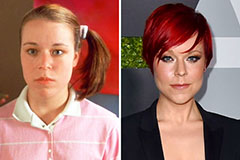 Tina Majorino Then & Now!
Tina Majorino Then & Now! Kerri Strug Then & Now!
Kerri Strug Then & Now!